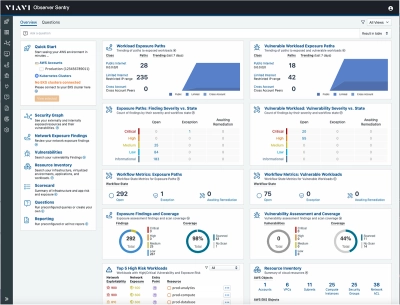
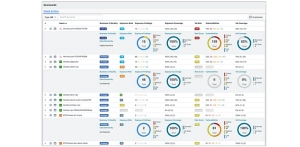
The VIAVI Observer Sentry Threat Exposure Management solution analyzes, models, and visualizes your AWS (Amazon Web Services) and EKS (Elastic Kubernetes Services) environments to help you proactively pinpoint where your cloud assets are exposed. Sentry’s intuitive views highlight misconfigurations, overly permissive settings, and risky combinations of exposure paths and vulnerabilities to specifically identify where to mitigate the risk of attack - prior to being compromised.
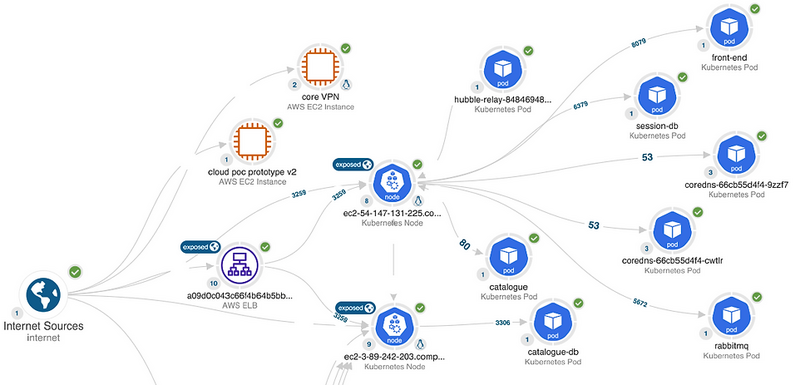
See your environment from the attacker's perspective with our attack path visualizations. Our exposure path analysis and advanced graph theory algorithms identify relationships between otherwise siloed security findings to continuously visualize and prioritize critical security gaps to better secure your cloud stack and ensure your team is working efficiently.
Threat Visibility
Leverage the integration of AWS VPC Flow Logs to gain a comprehensive view of traffic to and from exposed resources. This capability identifies attempted and successful connections, where they originated, and the volume of traffic associated with a conversation on an exposed port. Users can easily pivot to integrated threat intelligent data sources to assess whether malicious hosts are accessing exposed resources. The powerful combination of exposure and traffic visibility allows users to see beyond what could happen and understand what has happened.
Observer Sentry Features and Benefits Summary
- Attack and Exposure Path Management. Understand and visualize the entire AWS attack surface and attack paths within minutes by visualizing public Internet, cross-account, and cross-VPC exposures. Sentry identifies unknown or undesired access to cloud resources in an actionable context to quickly remediate and improve your cloud security posture.
- Maximum security, minimal effort. No need to deploy agents, AWS configuration data provides the ultimate source of truth. With minutes of effort, your teams can scan your entire cloud environment, map and visualize your assets and their relationships.
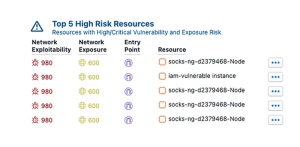
- Focus on risks that matter most. Detect, prioritize, and remediate critical exposures and attack paths in your cloud environment with Observer Sentry, continuously prioritizing critical risks based on the analysis of exposure, vulnerabilities, and other factors.
- Traffic provides critical visibility. Sentry integrates readily available VPC Flow Logs from the AWS environment for a deeper level of insight into high-risk exposures. Integrated traffic analysis allows your teams to determine whether suspicious hosts availed attack paths prior to remediation.
- Exposure reports to keep things simple. Public Internet, External Network Scan, Cross Account, Cross VPC, and custom service port exposure reports provide immediate visibility into exposed workloads with direct links that allow remediation to take place right from the report. Easily sharable, these interactive reports clearly identify what is exposed and how it is exposed, putting teams managing large scale AWS environments a click away from shrinking the attack surface.
-
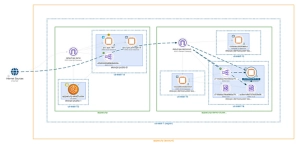
AWS + EKS Visibility
Connect to your AWS environment and EKS clusters in minutes. Our agentless approach continuously scans your AWS environment and its EKS and ECS (Elastic Container Service) clusters. Private EKS clusters can be connected via a Helm-deployed container. Observer Sentry maps provide highly intuitive cross-environment diagrams that quickly identify misconfigurations, overly permissive settings, and changes.
-
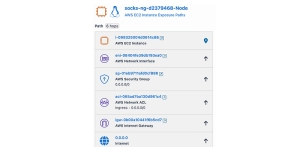
Exposure Path Management
Within minutes of connecting, see an automated list of Exposure Paths from various points of entry into your environment along with detailed hop-by-hop reachability to specific assets. Identify unknown or undesired access to assets or environments and take corrective action.
-
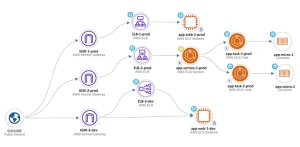
Attack Path Management
Attack Paths are the dangerous combination of exposure, exploitable network vulnerabilities and risky configurations that provide the paths of least resistance to high-value resources within your environment.
Attack Path management provides actionable context on your most critical issues, so your teams can proactively and continuously improve your cloud security posture.
-
Attack Surface Management
Observer Sentry creates a detailed inventory of your cloud assets and then performs an analysis to determine their attack surface, effective exposure, and risk. This analysis can also be applied collectively to logical groupings of assets that make up specific applications and workloads. These groupings are tracked in scorecards and visualized in attack surface maps.
Литература
Видео
Вебинары
Поддержка на каждом этапе работы
Мы оказываем техническую поддержку, предоставляем услуги, программы обучения и все необходимые материалы. Наша деятельность направлена на максимальное повышение отдачи от ваших капиталовложений в систему VIAVI.
Позвольте вам помочь
Мы всегда готовы оказать вам всю необходимую помощь.