Threat Exposure Management
Don’t just see potential attack paths; know what has been exploited and when with VIAVI.
In today's evolving cloud landscape, visibility is paramount for securing your digital assets against cyber threats. VIAVI Threat Exposure Management (TEM) powered by Observer Sentry redefines how you protect your AWS environment, offering a purpose-built solution that empowers you to swiftly identify, prioritize, and address unintended exposures and vulnerabilities. Our innovative approach leverages advanced analytics and visualizations, enabling you to understand your security posture with unprecedented clarity.
To better understand why VIAVI produced this unique approach to safeguarding your cloud environment, understanding the landscape in which TEM operates is necessary. The cloud offers exceptional flexibility and scalability, but it also presents a unique set of security challenges, leaving organizations vulnerable to a spectrum of cyber threats. Recognizing these common risks businesses face in the cloud is the first step towards implementing a robust and effective security strategy.
Understanding the Cloud Security Landscape: Common Challenges
TEM addresses many of the common security pain points customers encounter as they strive to keep up with ever-changing cloud environments and service architectures:
- Visibility Gaps: Ongoing human, system, and design changes make a passive approach to visibility unsustainable. Locking down systems reactively is not an acceptable approach for managing the interactions and permissive settings that may be creating new attack vectors.
- Siloed Views: The elimination of siloed views is one key to optimizing visibility. With customers maintaining multiple AWS accounts and VPCs, each with potentially large numbers of resources, monitoring these assets individually is neither efficient nor adequate.
-
Automated Changes: Automation and continuous expansion and improvements have heightened the pace of change in the end-to-end AWS environment to one that many teams struggle to keep up with.
-
Data Volume: Critical insights pointing to compromise can be obscured by the sheer volume of data, potentially leading to extensive delays in detecting and mitigating issues. The rate and complexity of data flows also makes it challenging to understand the impact of a breach without the benefit of intelligent analysis and Continuous Threat Exposure Management (CTEM).
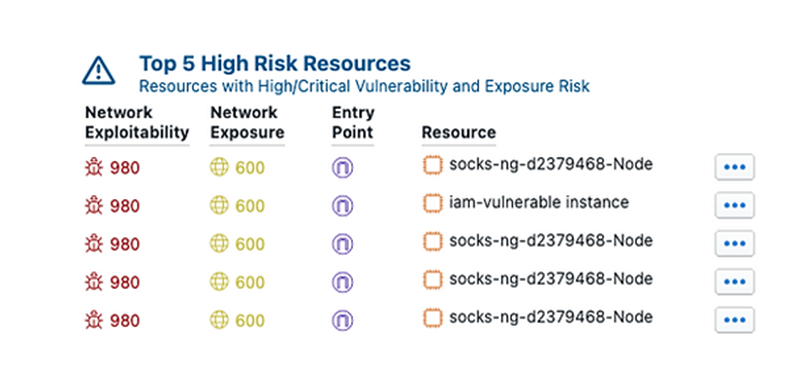
VIAVI TEM automates the process of discovering, analyzing, and visualizing AWS environments across all accounts. Click to enlarge
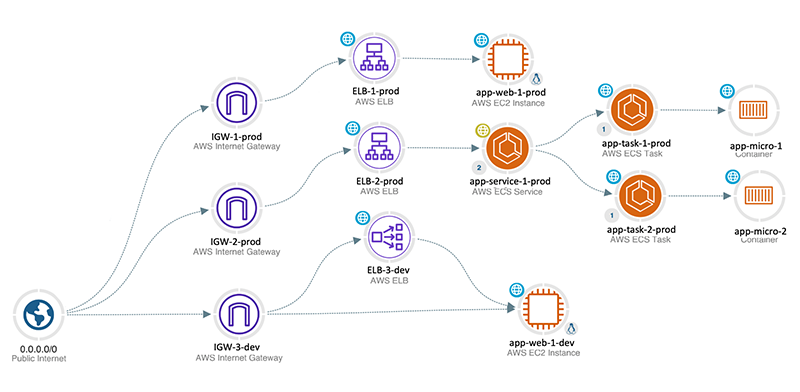
Exposure is inevitable, but it’s not always bad. What may appear to be an undesired exposure may simply be a necessary part of a service architecture and service delivery. Our unique blend of agentless technology, operationalized insights, and advanced automation extends beyond traditional security measures. It transforms your perspective, allowing you to continuously view your environment through the lens of an attacker. This shift from static lists to dynamic visualizations of your AWS ecosystem uncovers hidden interdependencies and vulnerabilities, facilitating a proactive defense strategy that keeps you ahead of potential threats.
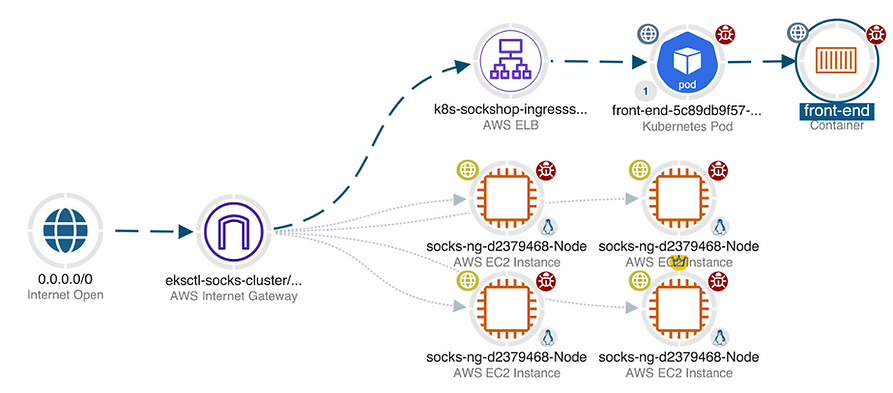
Attackers think in graphs - you need the ability to visualize attack paths that can be used to exploit vulnerabilities the way that they do. Click to enlarge
Attackers think in graphs, not lists. Think like your adversary. We change how you view your environment, taking it from lists, configuration details, and logs to a visualization of your AWS environment from the attacker’s perspective. VIAVI Observer Sentry identifies paths and interdependencies that linear protection strategies can miss, allowing you to visualize the relationships between assets and prioritize the most critical risks.
Traffic insights bridge the gap between seeing potential exposures and knowing what actually happened, allowing users to answer these critical questions:
- Did an attacker attempt to connect to an exposed resource?
- Was the attacker successful? Was it multiple attackers?
- Is there a breach? Was any sensitive data retrieved?
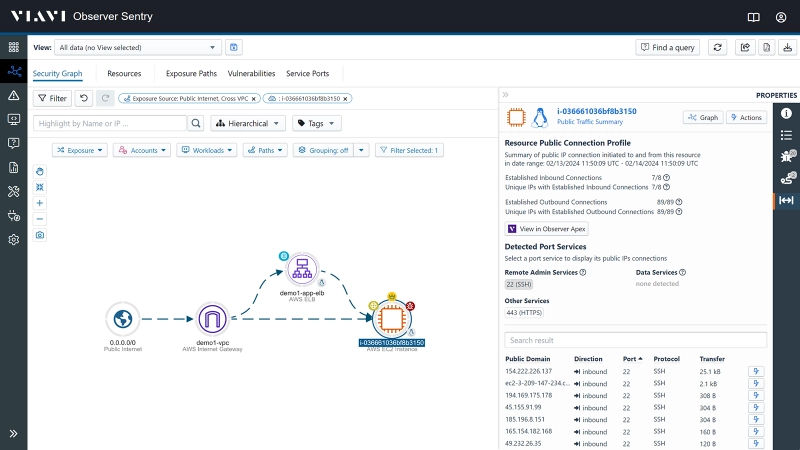
Security teams gain necessary insights into high-priority exposures by integrating detailed traffic and conversation history. Click to enlarge
Continuous Threat Exposure Management (CTEM)
Continuous Threat Exposure Management (CTEM) takes threat exposure management practices to the next level by continuously monitoring attack surfaces and assessing vulnerabilities. Gartner Research has identified CTEM as an effective, proactive approach to threat mitigation. Continuous threat exposure management practices include:
- Scoping the attack surface: This includes both the external attack surface and software as a service (SaaS) applications.
- CTEM discovery: Identifying less visible assets, vulnerabilities, and misconfigurations that were not considered during the initial scoping.
- Threat prioritization: Establishing a logical ranking system and prioritization algorithms for security risks.
- Validating attack pathways: Simulating attacks under real-world conditions to assess how the system reacts.
- Mobilization of resources: While automation helps to ensure threats are remediated quickly, resource mobilization considers the responsibilities of key human stakeholders.
Implementing CTEM processes in an ongoing cycle allows organizations to boost the value of their threat exposure management insights. Interdependencies, vulnerabilities, and exposure pathways are continually changing in the end-to-end AWS environment. This dynamic and flexible approach is necessary to address risks and vulnerabilities in real time.
Introducing Observer Sentry: The Heart of VIAVI CTEM
Observer Sentry stands at the forefront of our Continuous Threat Exposure Management solution, offering a unique ability to continually visualize, analyze, and prioritize cloud security threats. By mapping out the intricacies of your AWS environment, Observer Sentry delivers the insights needed to stay ahead of potential risks. It is part of the VIAVI Network Performance and Threat Solutions portfolio and the Observer Platform.
The VIAVI Observer Platform provides visibility into critical KPIs through pre-defined workflows and high-level dashboards. The versatile Observer Platform is optimized to support business goals while overcoming resource, technology, security, and asset management challenges throughout the IT enterprise lifecycle.
VIAVI Transforming Challenges into Opportunities
Continuous Threat Exposure Management allows users to improve their overall AWS security posture by continually reducing the attack surface. VIAVI addresses CTEM challenges by enhancing exposure visibility, presenting intuitive and actionable visualizations and reports highlighting risky combinations of exposure paths and vulnerabilities. We provide unmatched benefits to organizations navigating the complexities of the cloud.
Key Benefits:
- Agentless Technology scans the entire cloud environment automatically to map all assets and their relationships. The AWS environment and its EKS and ECS clusters are continually scanned to ensure cross-environment maps represent the latest threat exposure conditions.
- Operationalized Insights deliver intuitive, graphical views across your cloud ecosystem, enabling quick identification of misconfigurations and overly permissive settings, and facilitating an in-depth understanding of your cloud architecture.
- Traffic Visibility provides clear insights into network traffic enabling the detection of unauthorized access and the assessment of data compromise incidents with precision.
- Holistic Views allow users to view all accounts and VPCs and the interrelationships between them simultaneously while automating the process of auditing Security Groups, Access Control Lists, and Firewall Rules.
- Scorecards offer at-a-glance exposure level assessments for applications, logical asset grouping, workloads, or environments, enabling stakeholders to easily review and address areas of responsibility based on severity and criticality.
“Threat exposure management…expands beyond patches and automated blocking to better prepare against unpredictable threats and strategically reduce the enterprise’s attack surface” – Gartner Predicts 2023: Enterprises Must Expand from Threat to Exposure Management
Observer Sentry Answers the Right Questions
Asking the questions that impact cloud security the most will lead you to solutions that provide the greatest protection. Our CTEM solution, through Observer Sentry, helps you answer these important questions consistently and confidently:
- How does an attacker see my cloud environment?
The attack path analysis and advanced graph theory algorithms of Observer Sentry identify relationships between resources, allowing you to continuously visualize your cloud environment from the attacker's perspective and prioritize remediation of critical security gaps. - Where are my cloud assets at risk?
Observer Sentry creates a detailed inventory of your cloud assets and performs an analysis to determine their attack surface, effective exposure, and risk. This analysis can also be applied collectively to logical groupings of assets. - Which paths can attackers exploit? By quickly analyzing exposure paths from various points of entry and identifying unknown or undesired access to assets, the most exploitable paths are identified so that corrective actions can be initiated proactively. CTEM Scorecards and attack path maps provide actionable visual context.
- What do I fix first?
Observer Sentry continuously prioritizes critical risks based on the analysis of misconfigurations, network exposure, and vulnerabilities identified by 3rd party scanners and creates a prioritized list of risks for your cloud environment. - Have my exposure paths been exploited by an attacker?
With traffic visibility, users can determine with certainty whether any misconfigurations or unpatched vulnerabilities were exploited before they were corrected.
Discover the power of Observer Sentry in reimagining your approach to cloud security. Contact us for a personalized demo of Observer Sentry and explore the purpose-built benefits of our Threat Exposure Management solution in your AWS environment.
See more, know more, and stay one step ahead of potential risks.
Littérature
Laissez-nous vous aider
Nous sommes là pour vous aider à prendre une longueur d’avance.