What is Threat Intelligence?
Learn about Threat Intelligence and how to minimize detection and response times while enhancing overall network security.
Threat intelligence is defined as the evidence-based knowledge used to make informed decisions and prioritize organizational responses to known or potential cyber attacks. This includes a broad application of technical data, tools, and policies to minimize the risk presented by cybersecurity threats.
Unlike other more standardized cybersecurity disciplines like endpoint security, threat intel definitions and practices vary by organization. In general, the concept includes all efforts to improve security through incident response, reporting, and compliance remediation. Common elements of the process focus on data collection to prepare for, prevent, identify, and remediate security events.
To utilize threat intel in cybersecurity, each phase of the lifecycle should be optimized. Strategic data gathered from the network and throughout the process can also be used to inform subsequent phases and create a valuable feedback loop.
Protection
Protection is the fortification that a company builds to defend itself from intrusions like brute force attacks, advanced persistent threats (APTs), and malware. Deploying network security solutions from multiple vendors is a common approach for establishing broad protection from cyber attacks. Despite this emphasis on prevention, just one successful breach in millions of attempts is enough to wreak havoc. With these odds, it is more a question of when rather than if a breach will occur.
Detection
The detection phase begins once an intrusion has successfully eluded protection efforts. The tactics, techniques, and procedures (TTPs) used by hackers to conceal their presence in the network can be well camouflaged. For example, they may delete ARP/CAM tables to cover their tracks when they access the switch. Typical lateral movement by threat actors as they move through the network includes scanning IP addresses or DNS names to see what responds and sniffing packets to discover where valuable data is stored.
Effective detection strategies use recorded network data to map the history of what the suspect machine or user has done. With enriched-flow records collected, MAC addresses of known compromised machines can be entered into IP viewers to detect where else the hacker may have gone and what data could be affected.
Response
The response phase includes the actions taken after detection to:
- correct the problem
- contain the damage
- stop additional systems from being compromised
Once again, robust threat data capture, recall, and analysis are important tools for responding to security breaches quickly, leading to informed decisions that minimize the impact on operations.
Full-fidelity packet capture (PCAP) and enriched-flow analysis allow you to conduct historical analysis and determine the extent and consequences of a system breach. These intelligence sources are not limited by any distributed denial-of-service (DDoS) attacks or other data corruption from cyber attacks. Effective threat intel gathered from the network also creates a continuous improvement loop. In other words, the response information and intelligence gaps observed with each event can be used to inform future protection and detection strategies.
Cyber Intelligence Indicators of Compromise (IOCs)
A key to effective threat intelligence in each phase is the ability to recognize indicators of compromise (IOCs) quickly and accurately. These indicators are the forensic evidence that analysts use to characterize malicious activity. IOCs can include geographical irregularities, mismatched port-application traffic, unusual DNS requests, spikes in file read requests, automated web traffic, and many other network behavior patterns that fall within the tactics, techniques, and procedures of threat actors.
Indicators of compromise are not always easy to detect and evidence can range from basic metadata elements to extremely complex code. Data collection requirements including real-time monitoring for IOCs can improve protection and accelerate detection. This data collection and analysis also reduces response time and adds to the pool of strategic intelligence necessary to prevent reoccurrence.
How Can Your Organization Benefit from Cyber Threat Analysis?
Threat intelligence can produce ongoing benefits for any organization. This is especially true during the detection and response phases. Access to enriched-flow records and individual packet data greatly reduces the time required for analysts to detect malicious activity and lateral movement patterns. High visibility into user, IP, and MAC relationships means other impacted devices can be quickly identified, to ensure customer exposure is minimized.
Investigation efficiency leads directly into cost savings during the response phase. Studies have shown that breach response cycles of less than 200 days are on average $1.2M less costly than those spanning 200 days or more. Actionable network insights are at the heart of this improved efficiency. Recorded threat data is proof of what was exfiltrated, when, and how much. Reporting costs and regulatory fines from privacy legislation like GDPR and CCPA are also minimized through detailed data capture and reduced response times.
What Does Threat Data Show You?
Threat intelligence using flow-based solutions goes far beyond basic status reports. Optimized threat intel adds more tactical intelligence to the flow-based capture. Multiple types of threat intelligence data can also be combined to form a more complete picture of the threat landscape.
Integrating technical authentication details from Active Directory, IP addresses from NetFlow, MAC addresses from ARP tables, and cloud data improves network visibility. Backed by full-fidelity forensics, enriched flow-based data also allows IP blacklists and traffic profile baselines to be continually updated and improved.
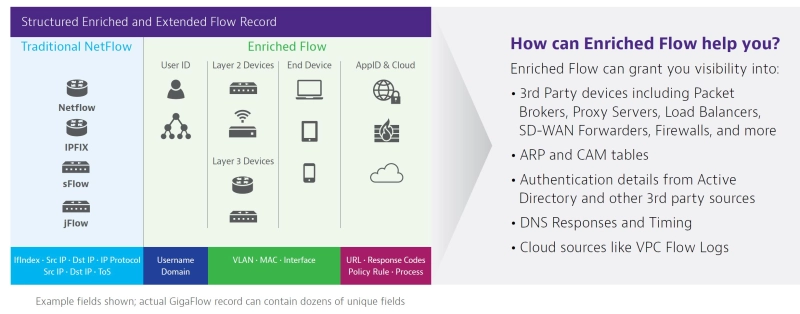
Cybersecurity intelligence data can be used to produce real-time threat maps that drill down to specific network monitoring use cases. This includes intel on who is (or was) using the rogue device and where it is located. Threat maps also include the communication history of the rogue device. This can be used to pinpoint root cause and exposure levels. Full packet capture can then be used to "rewind" directly to critical moments of the breach so that detailed network conversations can be analyzed.
Vulnerability management is closely related to threat intelligence. Vulnerabilities within web applications or network infrastructure are what bad actors rely on to gain entry. Although vulnerability threat intelligence is an important part of an integrated strategy, the two processes have important differences.
Vulnerability management is essential for protection and detection efforts. Penetration testing or pen testing is a common practice for subjecting the network to attempted breaches that simulate real-world global hacking. Based on the results, security patches and other vulnerabilities were prioritized and deployed to improve detection.
Threat intelligence can be used to develop IP blacklists and threat profiles as shown below. Historical records of the tactics, techniques, and procedures used by intruders can also be used to prioritize protection based on the latest trends. This application of strategic intelligence shows the potential of data-centric cyber threat analysis.
A top threat intelligence platform combining user-centric flow analysis and deep packet capture enables the potential of both types of threat intelligence to be realized. VIAVI has developed industry leading tools to optimize detection and response cycles along with overall network security. These solutions should be front and center in your arsenal of cybersecurity protection.
Observer GigaFlow
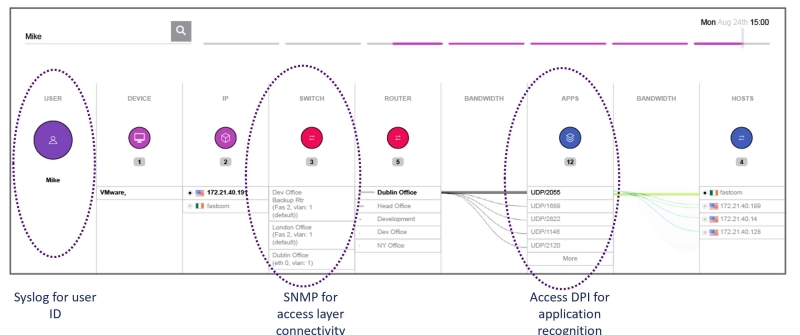
Using a mixture of authentication tools makes it difficult for analysts to quickly trace host device identification, location, and communication channels when IOCs are detected. Observer GigaFlow improves tactical intelligence by combining infrastructure, network, and user data into enriched-workflow records that are continually stored for convenient recall. Unauthorized device intrusion, lateral movement, or other rogue activities are identified in seconds, rather than hours or days.
The GigaFlow interactive IP Viewer provides a window into network application, user, IP, and MAC relationships. Simply entering a host device or username produces instant Layer 2 and 3 device and application usage information. This includes network infrastructure elements that do not generate conventional flow data.
Observer GigaStor
Packet capture is a threat intelligence detection and response tool that streamlines troubleshooting and reduces dwell time. The VIAVI Observer GigaStor is the industry-leading packet capture appliance. Blazing wire capture and data mining speeds can easily keep up with the fastest enterprise networks. Each stored packet contains detailed breakouts of network conversations and transactions that can be recalled during the security breach response phase.
Once intrusive software or malware has eluded the intrusion detection system (IDS), it can move quickly throughout the network as it probes internally. Backdoors that elude normal authentication might be used to leave without a trace. Using packet capture, a permanent and detailed record of this activity can be recalled days or weeks later. The location and impact of the initial breach can be identified quickly to minimize dwell time and user impact.
Why is Having Comprehensive Network Visibility Critical to Threat Intelligence?
When solving a crime, multiple eyewitnesses, forensic evidence, and fingerprinting can lead to an open and shut case. The same concept applies to cybersecurity intelligence. Enriched-flow data and packet capture intelligence sources combine to form a clear picture that shines a spotlight on threat actors and their tactics. Comprehensive threat data is equally useful for breach remediation and repair.
Events like DDoS attacks leave fingerprints, with thousands of connection attempts flooding a service at once. Packet capture produces permanent forensic records of these events that can be reconstructed to analyze the attack and prevent future occurrences. A threat intelligence platform that combines enriched-flow data and packet capture can pinpoint where the bad actor got in, whether they are still there, and how the problem can be fixed quickly.
Why Intelligent Tools for Network Detection and Response are Critical for Securing Your Organization
Office communication and networking are morphing into a conglomeration of commercial networks, private users and devices, and an increasing reliance on cloud computing. This new reality leads to a mixture of private/personal application usage, unprecedented geographical disparity of network users, and more unsecured endpoints. These endpoints are ready targets for hackers, accelerating the need for comprehensive threat intelligence in cybersecurity.
The cost of cyber threat intelligence gaps can be measured in stolen data, regulatory fines, and system downtime. The loss of hard-won reputation and consumer confidence in your business team can be even more valuable and harder to regain. With cyber attacks now an ongoing reality, having the right threat intelligence tools to preserve customer perception makes good business sense.
The Future of Threat Intelligence in Cybersecurity
The unexpected acceleration of remote workplace systems is an example of unplanned changes stacked upon planned shifts in the network landscape. The IoT adds a new layer to the threat landscape, with endpoints ranging from medical devices to automobiles and trains. Cyber threat intelligence must continuously protect users and their data from threat actors. This will include a growing number of objects and services vulnerable to theft, tampering, and privacy intrusion.
Cybersecurity attacks will certainly continue to grow in number and sophistication which is why enhancing security operations is crucial. The recent Sunburst attack is an example of why there is a need to have an evidence-based approach to managing cyber risk. Telecommuting has coincided with a spike in malicious cyber attacks, and this uptick in activity is not expected to end any time soon. Economic conditions, access to technology, and anonymity entice more bad actors to join the fray each day, with a new cyber attack occurring every 39 seconds. However, when enriched flow records and packet data are utilized to their fullest potential, the enormous risks these trends represent can be addressed successfully.
Related Resources
-
White Papers & Books
How a NetOps/SecOps Alliance Can Outmaneuver the Enemy: Winning the Security Battle -
Blog
What the NASA Cyberattack Teaches Us About Simple Technologies and Advanced Threats -
White Papers & Books
NPMD for Network Security Forensics -
White Papers & Books
Using Wire Data for Security Forensics