Observer Threat Forensics
Powering NetSecOps shared insight for fast detection, seamless collaboration, and effective resolution
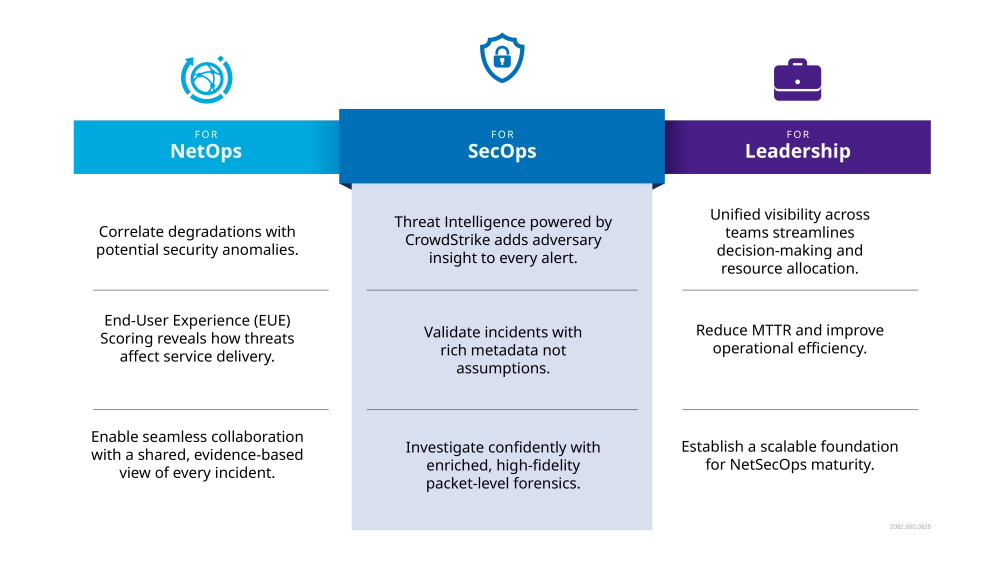
Observer Threat Forensics delivers threat intelligence and packet-level visibility to enrich security analytics, accelerate investigations, and unite NetOps and SecOps around shared insight.
Security Operations Centers (SOCs) face overwhelming alert volume, fragmented visibility, and insufficient context. Analysts must sift through thousands of signals to identify what truly matters, often without the packet-level evidence or service impact insight needed for confident identification and response.
Observer Threat Forensics with threat intelligence powered by CrowdStrike® bridges this critical gap. This dedicated cybersecurity solution, extends the trusted Observer platform beyond performance monitoring into advanced network-based threat detection and forensics. Powered by integrated Observer Threat Intelligence, it enriches every alert with multi-layered context including tactics, infrastructure, geolocation, and behavioral indicators for faster, more precise, and collaborative investigation across network and security teams.
Threat Intelligence Meets Forensics
Observer Threat Forensics combines real-time threat intelligence with packet-level analysis and rich metadata to expose hidden risks, validate alerts with precision, and give SecOps and NetOps a unified view for faster, more confident response from a single source of truth.
Real-Time Threat Intelligence Correlation
Detect with precision.
By continuously correlating live network traffic with dynamic threat intelligence, Observer Threat Forensics quickly identifies known indicators of Compromise (IOCs) and adds context around malicious behaviors, exploited vulnerabilities (CVEs), and attacker TTPs. Each alert is prioritized by relevance and potential impact empowering analysts to act faster and more effectively.
Forensic-Level Investigation
Validate threats with confidence.
Every alert includes a direct link to packet-level evidence, including detailed metadata revealing the who, what, and where behind suspicious activity through attributes such as Ips, domains, protocols, and URLs. This provides analysts irrefutable visibility into the event. Analysts can rapidly identify patterns, visualize behaviors over time, and validate findings without always needing to drill into raw packets. When deeper proof is required, packet-level evidence provides definitive confirmation of what occurred, enabling complete reconstruction of the attack sequence. This layered approach—metadata for speed, packets for proof—delivers both agility and forensic certainty across every stage of investigation.
Comprehensive Visibility
See everything that matters.
Full-spectrum visibility starts at the packet. By capturing and analyzing both packet and flow data, Observer delivers a complete view of every device, conversation, and communication path, helping teams uncover hidden threats, abnormal behavior, and lateral movement before they disrupt critical services.
Faster Mean Time to Identify (MTTI)
From detection to clarity in record time.
Automated correlation between packets, flows, and threat intelligence accelerates the identification of true incidents by cutting through alert noise and manual data stitching. Each alert is enriched with contextual metadata and links directly to relevant packet evidence and performance data, accelerating validation, containment, and remediation to help minimize business disruption.
Retrospective Analysis
Rewind and uncover what was missed.
Long-term packet, metadata, and flow retention enables retrospective detection of zero-day exploits (exploits = unknown) and persistent adversaries, allowing analysts to examine historical traffic and identify activity that was previously unknown or unrecognized during initial analysis.
How It Works
- Forensic-Grade Alerts and Enrichment
High-fidelity alerts are generated directly from packet and flow analysis, enriched with continuously updated threat intelligence. Each detection includes contextual details such as associated IPs, indicators of compromise, and behavioral patterns for faster triage. - Built-In Adversary Context
Each alert provides critical threat information, such as, key IOCs, including attacker tactics, techniques, and procedures (TTPs), known command-and-control infrastructure, and exploited vulnerabilities (CVEs). This context enables analysts to prioritize investigations, assess severity, determine relevance, and prioritize investigations with confidence. - Real-Time Correlation, Zero Manual Stitching
Network activity is automatically correlated with threat intelligence data to surface high-confidence detections. Analysts gain immediate visibility into who, what, and how — without manual log or data correlation. - Linked Packet Evidence for Immediate Validation
Every alert is directly tied to underlying packet data, allowing analysts to pivot seamlessly into full forensic capture for verification, root-cause analysis, and impact assessment — all within Observer Apex . - Unified View for NetSecOps Collaboration
Packet-level forensics, flow analysis, and threat intelligence are consolidated into a single dataset, enabling network and security teams to view, validate, and respond from a shared operational perspective—without changing their existing workflows. Observer presents insight in the context most relevant to each team, whether focused on network performance or security investigation.
The convergence of network and security operations is no longer optional, it’s essential. Observer Threat Forensics delivers the capabilities that make this collaboration real, supporting use cases that align detection, analysis, and response through shared data and unified workflows.
Use Cases
Data Sheets
Let Us Help
We’re here to help you get ahead.