What are Data Center Security Requirements?
Learn all about the requirements for keeping data centers secure, operational guidelines, compliance, and more.
Data center physical security encompasses all methods used to protect data and hardware from outside interference, theft, or corruption. Unlike cybersecurity measures to prevent and detect virtual attacks originating from external endpoints, physical security practices address direct threats to facilities and hardware.
- Organizations that rely on data centers to remain viable should establish physical data center security policies to manage all personnel and assets that enter or leave their facility.
- Equipment and tools brought into data centers are closely monitored to prevent the disruption of server, router, switch, or data center interconnect (DCI) functionality.
- Data Center Access is extremely limited in most instances, with few entry points, 24/7 security guards on duty, video surveillance, and employee badges and/or biometric readers in use.
Data centers are categorized into tiers ranging from level 1 to 4, based on the ANSI/TIA-942 standard. Tier 1 is typically assigned to less complex, small business data centers while Tier 4 designates a large enterprise or cloud data center with a 99.995% uptime requirement and high levels of redundancy. Data center security requirements are accordingly more stringent for Tier 3 and 4 centers.
- Hyperscale Data Centers: Large-scale distributed computing centers support high volume data processing, computing, and storage. These centers establish multiple layers of physical security to prevent unauthorized access. These measures include reinforcement of data center walls and detailed hardware destruction protocols.
- Private High-Security Data Centers: Privately owned data centers are less constrained by external data center security standards, although Tier 4 standards are often adopted to safeguard data and brand integrity. A thorough risk assessment weighs the likelihood of a security breach vs. the impact.
- Government Data Centers: Public agencies maintain a trove of sensitive personal data or highly confidential intelligence within their data center walls. These institutions establish the highest possible level of physical security through additional access and facility restrictions.
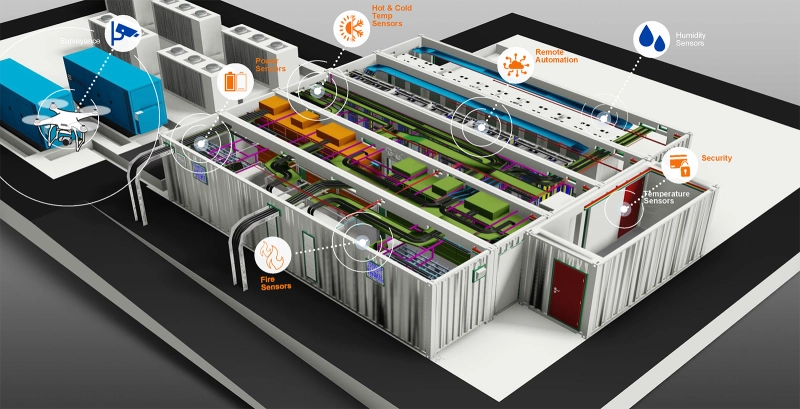
- Data Center Infrastructure: Successful large-scale breaches are reminders that all aspects of data center infrastructure must be monitored and reviewed. This includes everything from HVAC and power systems to perimeter fencing and geographic location.
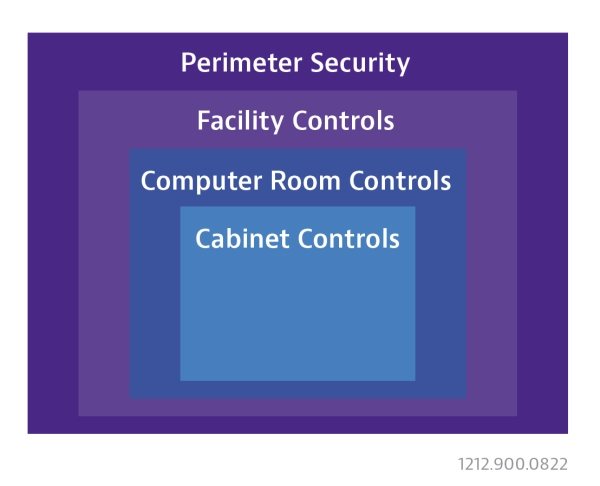
Each data center establishes and abides by multi-faceted operational guidelines. Physical security is one element of data center operations that also include safety, maintenance, monitoring, power distribution, and cooling.
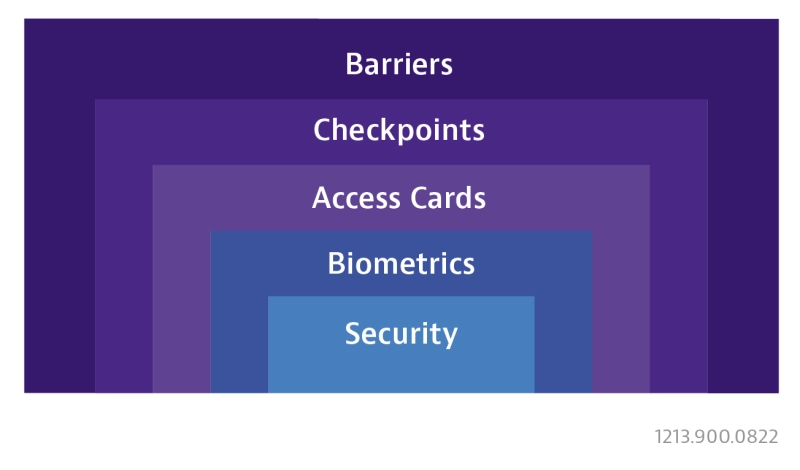
- Multi-factor Identification: Redundant checkpoints are used to control and monitor who enters or leaves each area of the data center. In addition to facility constraints that limit entry points, badging, pin codes, fingerprints, and retinal scanning are among the methods used to restrict access.
- End-of-life equipment: Hardware disposal is subject to procedures and oversight to ensure all hard drives and other data storage devices are wiped or destroyed. Only approved disposal services can be utilized, and detailed records must be maintained for each component.
- Red Zones: This designation is assigned to areas within the data center where customer data is being processed. Red Zone security protocols typically prohibit the introduction of hardware with active wireless communication features. Tamper-evident security tape might also be applied to cover data ports on 3rd party (test) devices.

Hyperscale / Public Cloud Security
The hyperscale definition provided by the IDC states a minimum size of five thousand servers on a ten thousand square foot or larger footprint. Many public cloud data centers fall into this category. While these immense proportions lead to improved efficiency and built-in redundancy, the high concentration of data also heightens physical security concerns.
- Colocation is increasingly common as hyperscalers manage the data of multiple clients and lease excess capacity to tenants. While customers benefit from the multi-layered controls of a secure data center, additional oversight and boundaries must be established.
- High-speed Interface standards commonly utilized in hyperscale / public cloud architecture are also susceptible to physical attack. Both the PCI Express (PCIe) and Compute Express Link (CXL) interfaces incorporate security features to protect links from data center threats and vulnerabilities.
- Unmanned data centers made possible through 5G and the IoT improve physical security simply by reducing the number of facility visits. Lights out data centers also leverage the IoT for automated 24/7 surveillance using robots or drones.

Private High-Security / Government Data Centers
Regardless of the external requirements, private high-security and government data centers maintain elevated security standards based on the intolerable risk associated with a physical breach.
- Government agencies including the IRS, FBI, and Defense Department have taken steps toward outsourcing data center management and transferring assets to the cloud. This places the onus on hyperscalers to physically isolate sensitive data and strengthen security infrastructure accordingly.
- Security testing and auditing are used to verify system integrity. Entry points, surveillance equipment, and physical barriers in high-risk data centers must be subject to frequent inspection. Trained specialists perform physical penetration testing to uncover any system weaknesses.
- Government and high-security locations often impart strict data center physical security standards for 3rd party equipment, prohibiting devices with wireless communication functionality in all areas of the facility.
- Private data centers often benefit from the absence of server or facility sharing by outsiders. This allows more focus to be placed on insider threats and the “fourth layer” of protection, which includes cabinet locking mechanisms and data logs.
External standards provide a set of best practices for organizations seeking to maintain a secure data center. The globally adopted ANSI/TIA-942 standard defines minimum data center design and installation guidelines. The ISO 27001 standard provides valuable guidance for the implementation of security controls and the identification of risks and vulnerabilities.
Data center security compliance also encompasses HIPAA, PCI DSS, and other industry-specific standards designed to protect the privacy of consumer data. While each organization establishes their own unique data center security requirements and policies, adherence to recognized standards is essential for establishing legal compliance in the event of a breach.
Data Center Threats
Despite the increased focus on cybersecurity measures, threats to an IT data center infrastructure can be equally severe. The same vigilance used to optimize firewalls and encryption techniques should be applied to combat physical data center threats.
- Insider Threats: Identity theft and misguided employee intentions are unavoidable issues that pose a direct threat to physical security. Improved visibility and artificial intelligence (AI) are among the tools used to mitigate these threats.
- Multi-layered Attacks: Hybrid forms of attack can disrupt software-based physical access controls or steal security credentials through well-orchestrated cyberattacks. These complex data center threats and vulnerabilities call for a holistic approach to security and asset protection.
- External Devices: Personal items and test devices, particularly those capable of recording, storing, or transporting data wirelessly, represent a threat that must be mitigated to install and maintain data center hardware. Strict control measures may include the disabling or complete prohibition of wireless capabilities and data ports.
Data Center Testing
VIAVI has established a suite of portable, fully automated data center test solutions. These forward-looking devices address data center security and compliance concerns with user-selectable deactivation of RF-emitting functions.
- Fiber Monitoring: The volume of fiber within and between large data centers creates an intricate web of physical security endpoints. Fiber inspection, certification, and monitoring processes are essential elements of data center testing.
- OTDR: Cloud and hyperscale data centers are ideal settings for automated OTDR testing to characterize and diagnose fiber links. VIAVI offers advanced multi-purpose, portable OTDR testers along with permanent rack-mounted solutions to monitor the network and trigger alarms automatically when fiber is compromised.
- MPO Connector Testing: Cloud data center density constraints have led to the rapid adoption of MPO connectors for patch panel, server, and switch connections. VIAVI provides comprehensive test solutions with native MPO connectivity intended for high-density fiber environments.
- Use Case #1: Test Equipment Controlled by Data Center
In this scenario, the test equipment is purchased by the data center directly. Since the equipment is fully dedicated to in-house use, it can be pre-configured to safeguard physical security and remain inside the data center near the designated point of use.
Data transfer can be completed using a direct USB or Ethernet connection to a local PC. This method enables the data center end-user or approved 3rd party contractor to maintain full control and visibility of label lists or test profiles pushed down to the test equipment, as well as test reports and other information pulled off the test device. - Use Case #2: Test Equipment Controlled by Contractor
In these instances, the test equipment is owned by the contractor and used for additional applications outside of the data center. The equipment is therefore subject to physical security protocols prior to entering the data center. The first step is a pre-approval process for the specific equipment type, which can vary by data center. The next step is the application of tamper-evident security tape to cover all connection ports on the device before entering the red zone.
Upon completion of testing, the security tape is removed. However, the equipment may be retained by the data center security department for an additional review lasting several days, making it impossible for the technician to retrieve collected data and test results. This can potentially lead to an “at risk” data center turn-up while the test results are pending.
How VIAVI Supports Data Center Security Requirements
Data center security relies on a robust combination of physical measures to limit contact with hardware and cybersecurity tools to nullify virtual threats. VIAVI has established an industry-leading suite of data center test solutions designed to accommodate stringent access and compliance requirements.
The migration to cloud architecture has multiplied data center physical security endpoints and complicated access and surveillance protocols. At the same time, accelerated construction timelines, high speeds connectivity, and DCIs running near full capacity have made data center testing and monitoring more important than ever.
VIAVI ensures data center uptime and reliability with versatile test solutions that complement the physical security and compliance standards of hyperscale, government, and private high-security data centers.