5G Network Slicing
Understand the challenges and opportunities of 5G network slicing.
What is network slicing in 5G?
Network slicing is a telecommunications configuration that allows multiple networks (virtualized and independent) to be created on top of a common physical infrastructure. Each “slice” or portion of the network can be allocated based on the specific needs of the application, use case, or customer. This topology is an essential element of the 5G architectural landscape.
While services like smart-parking meters require high reliability and security, other 5G use cases (like driver-less cars) need ultra-low latency (URLLC) and high data speeds. Network slicing in 5G supports these diverse services and reassigns resources as needed from one virtual network slice to another, making the one-size-fits-all approach to service delivery obsolete.
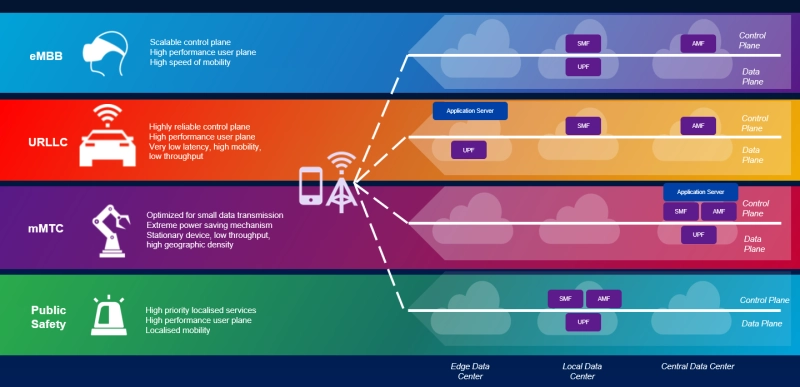
Architecture
Network slicing architecture in 5G is analogous to a complex public transportation system. Rather than using multiple rows of identical lanes and automobiles, some transportation elements (such as roads and bridges) are universal while others are tailored to the speed, budget, and volume requirements of the users. Each network slice utilizes many common network elements, but E2E (end-to-end) network slicing and logical isolation from other slices are essential.
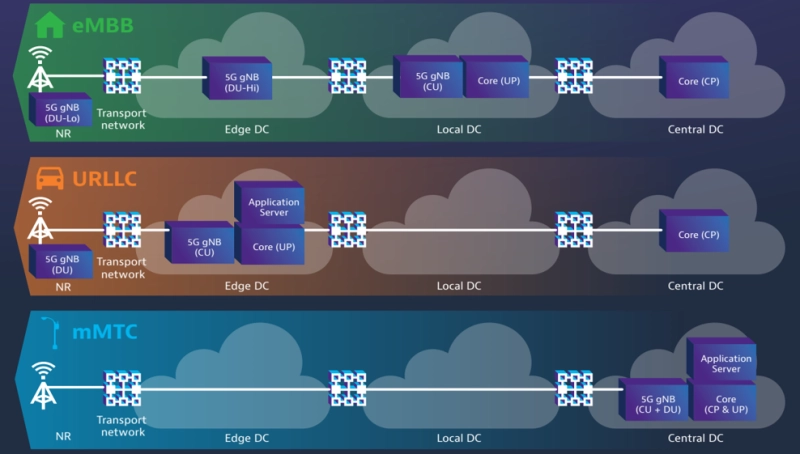
- NFV (network function virtualization) moves network functionality to virtual machines (VMs) on virtualized servers. NFV is a key element of network slicing architecture.
- SDNs (software defined networks) are used to manage network slicing traffic flows through the application program interfaces (APIs) of a central control plane. They also control the provisioning of VMs in edge or core clouds.
- The control plane configures resources so that tailored services can be provided to the client through the application layer.
- Recursion is a key feature of network slicing SDN. Recursion allows the control plane to create multiple sub controllers to support slice composition.
- The network slice controller (orchestrator) maps services and monitors the functionality between other layers.
- S-NSSAI (Single-Network Slice Selection Assistance Information) allows the network to detect a specific NSI (network slice instance). This information defines how a slice should behave and what differentiates it from other slices.
Through SDN virtualization, each client instance can unlock and orchestrate the resources needed to create a slice with the correct service(s) included. This flexibility is the key to enabling the three, core network slice/service types:
- Enhanced Mobile Broadband (eMBB)
- Massive Machine Type Communications (mMTC)
- Ultra-Reliable Low Latency Communication (uRRLC)
3GPP Network Slicing
The 3GPP has recognized network slicing as an essential component of 5G. Slicing has been an ongoing focus for working groups developing 5G core architecture. 3GPP technical specification (TS) 23.501 defined 5G system architecture with slicing included, while TS 22.261 specified the provisioning of network slices, association of devices to slices, and performance isolation during normal and elastic slice operation.
Basic network slice lifecycle management features were introduced in Release 15 of the 3GPP 5G specification. Release 17 defined a closed loop mechanism to support multiple SLA requirements and introduced network slicing energy efficiency KPIs. 3GPP Release 18 will establish rules for third party slice usage based on UE quantity, load, and time limits.
Challenges and Opportunities
The benefits of network slicing are self-evident, since a single network can be divided to cover many use cases based on customer demand and segmentation.
- Operators can allocate resources to each slice individually to produce the speed, throughput, and latency needed to cover the breadth of network slicing in 5G.
- Offering network slices as a service minimizes operating expenses (OPEX) and capital expenditures (CAPEX) for operators.
- Critical public entities, such as first responders and medical emergency teams, can be prioritized with respect to coverage, capacity, and connectivity.
- Network slices can be initiated and deployed within minutes to serve the needs of temporary use cases like concerts and other gatherings.
AI-powered orchestration provides a secure and efficient alternative to test and deploy new services. With the network divided, it is no longer necessary to disrupt existing services to assess new ones. T-Mobile launched the first 5G network slicing beta for developers of video calling applications in August of 2023.
The ChallengesDespite the obvious upside, there are still many challenges that remain for operators and developers. Full E2E network slicing includes implementation in the radio access network (RAN). While network slicing is possible on non-standalone (NSA) 5G networks leveraging legacy 4G LTE architecture, standalone (SA) RAN architecture is required to enjoy the full benefits.
Progress towards standardization continues, although full industry consensus on network slicing deployment on 5G networks with other architectural elements has not yet been attained. In addition, more mobile device offerings must incorporate 3GPP-based route selection policies (URSP) to enable the navigation of multiple network slices and encourage adoption by operators.
The addition of more networks over the same physical infrastructure also creates added stress for operators. Maintaining SLA, QoS, and security assurance for each individual slice and managing the spectrum slicing and allocation under dynamic conditions are additional challenges.
Security
Slicing complexity also extends to network security considerations. Each slice has unique security requirements based on the use case and requires its own device authentication to validate users. The scaling factor associated with network slicing introduces billions of potential new attack vectors. A successful attack from a central 5G network management point can infiltrate many slices and/or network domains simultaneously.
- Security responsibilities between operators and enterprises utilizing the slice must be clearly established.
- Innovative strategies for security, such as micro-segmentation, continue to evolve to meet this need.
- The US National Security Agency (NSA) published guidance on 5G network slicing security in July of 2023 that includes zero-trust architecture, confidentiality, and NSSA leakage over the air.
- Security-as-a-service (SECaaS) vendors are developing comprehensive network slicing security solutions that support all stakeholders.
Use Cases
Although the list of 5G applications seems limitless, most use cases fit into one of three categories:
- Enhanced Mobile Broadband (eMBB) transports large amounts of data across a wide coverage area to support services like high-definition streaming and virtual reality on the go. Throughput, mobility, and a scalable control plane are key features of eMBB.
- Massive Machine Type Communication (mMTC) supports data transfer for large numbers of mobile or stationary devices with low data rates to empower the internet of things (IoT) or machine-to-machine communication in factories and warehouses.
- Ultra-Reliable Low Latency Communication (URLLC) is the key to use cases like drone control and remote robotic surgery that require extremely low latency and exceptionally high reliability (up to 99.999%). For URLLC, the UPF (data plane node) should be located close to the network edge to reduce latency.
Advanced applications including Vehicle-to-Everything (V2X) and smart factories combine elements of all three use case types as more features and functionality are integrated each day.
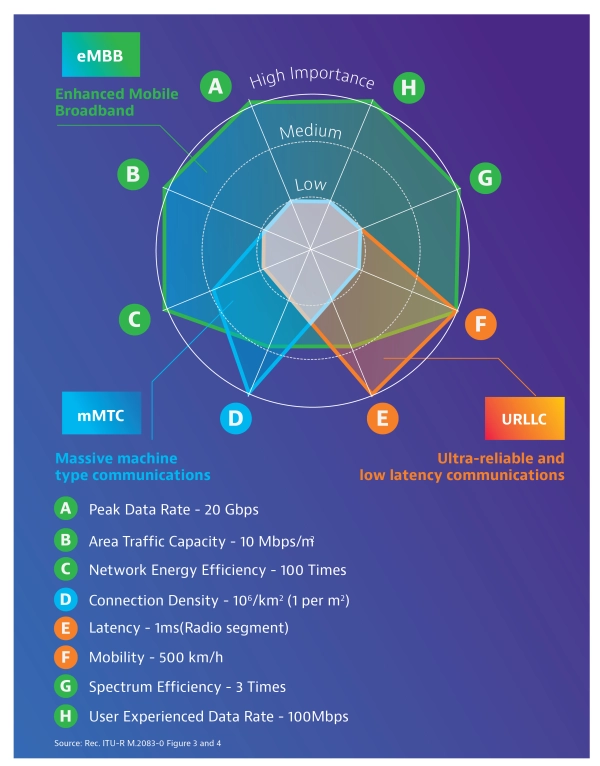
While the IoT is sometimes perceived as a single use case with a uniform set of requirements, the variety of potential IoT applications will increase 5G network slicing diversity. Some IoT devices will have flexible latency requirements, while remotely operated surgical or medical monitoring equipment places life-or-death importance on reduced latency. Public safety devices, such as smoke detectors and surveillance cameras, require prioritized traffic routing and higher levels of security that can be enabled within the network slice.
Network Slice Testing
The diversity of network slicing use cases highlights the need for E2E test and validation. Essential test practices include:
- 5G core network emulation
- Network slice functionality verification and node selection
- Simulation of the variety and volume of devices
When testing network slices, it is important to confirm the correct nodes were selected and the slice functions as expected while supporting a variety of devices and systems. Since testing network slices with real-world infrastructure and millions of devices is not feasible, VIAVI has developed end-to-end, RAN to Core test solutions capable of emulating individual nodes and the 5G network overall.
The TeraVM is an ideal software-based tool for 5G security validation and application emulation. The TeraVM is 100% virtual and can emulate a city’s worth of 5G network subscriber activity and easily pinpoint flow problems and bottlenecks.
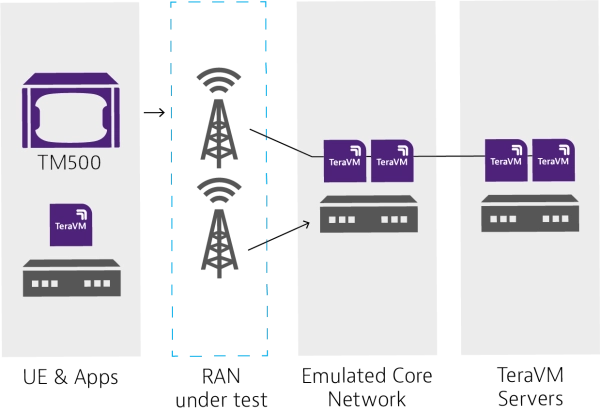
The TM500 test system is another powerful solution for validating network performance as experienced by end users. The TM500 can support millimeter wave frequencies and emulate hundreds of thousands of UEs in either standalone or non-standalone modes.
Combining TM500 with TeraVM provides a comprehensive network slicing test method that is unique in the market. Both the TeraVM and TM500 are recognized as industry leading 5G tools used to perform the first wrap-around testing of 5G standalone (SA) base station equipment.
Along with the revolutionary speed and bandwidth improvement of 5G, the services enabled by network slicing create wholesale changes in medicine, transportation, manufacturing, and many other industries. The 5G highway will soon be overloaded with traffic in all shapes and sizes, so utilizing test tools to proactively to verify functionality is a prudent course of action.
Learn about 5G VIAVI today!
Are you ready to take the next step with one of our 5G test products or solutions?
Complete one of the following forms to get going:
